How to Deploy FortiClient VPN and Profiles via Microsoft Intune: A Step-by-Step Guide

In this step-by-step guide, we will walk you through the process of deploying FortiClient VPN and profiles using Microsoft Intune. FortiClient VPN is a powerful tool that allows users to connect to a virtual private network (VPN) server, providing secure and encrypted access to internal resources. With Microsoft Intune, you can easily manage and deploy FortiClient VPN and profiles to your organization’s devices, ensuring a consistent and secure connection for all users.
The first step in deploying FortiClient VPN is to create the transform file, which contains the necessary configuration settings for the installation. The transform file is a string of settings that can be used to customize the installation process without modifying the original installation package. This allows you to configure the installation to meet the specific needs of your organization, ensuring a seamless deployment process without any manual intervention required.
Creating the transform file is a straightforward process that can be done using a variety of tools. For this guide, we will be using the Windows Installer XML (WiX) toolset, which provides a set of utilities for creating and managing MSI installation packages. WiX offers a powerful scripting language that allows you to define components, features, actions, and other elements of an installation package, making it an ideal choice for this task.
Before we begin, it is important to note that FortiClient VPN is available for free from the Microsoft Store. However, the version available in the Microsoft Store is a trial version, and it may not include all the features and capabilities of the full version. If you require access to all the features of FortiClient VPN, it is recommended to download the full version from the Fortinet website.
Step-by-Step Guide to Deploy FortiClient VPN and Profiles via Microsoft Intune
1. Preconfigured Scripts
To deploy FortiClient VPN and profiles via Microsoft Intune, you’ll need to use preconfigured scripts. These scripts will automate the installation process and allow you to easily manage the VPN connections and profiles on your devices.
2. Five Installation Scripts
You’ll need five installation scripts to deploy FortiClient VPN and profiles: FortiClientVPN.msi, LetsConfigMgrVPN.ps1, InstallFortiClientAndProfile.ps1, RebootReallySuppress.ps1, and RemoveVPN.ps1. These scripts will handle the installation, configuration, and removal of the VPN connections and profiles.
3. System Requirements

Before deploying FortiClient VPN and profiles, make sure that your devices meet the system requirements. This includes having the necessary prerequisites installed, such as PowerShell and the Win32-AppxPackage management scripts.
4. VPN Gateway Configuration
To configure the VPN gateway for FortiClient, you’ll need to specify the VPN gateway address and port, authentication method, and other settings. This information can be obtained from your network administrator or IT department.
5. Profile Configuration
Once the VPN gateway is configured, you can create the VPN profiles. These profiles define the specific settings for each VPN connection, such as the VPN gateway, username, password, and other options. You can create multiple profiles for different VPN connections.
6. Deploying the Scripts
To deploy the scripts via Microsoft Intune, you’ll need to create an application package and assign it to the target devices. This will trigger the installation of FortiClient VPN and profiles on the devices.
7. Testing and Troubleshooting
After the deployment, it’s important to test the VPN connections and profiles to ensure that they are working correctly. You may also need to troubleshoot any issues that arise during the deployment or configuration process.
8. Streaming and Kodi Setup
If you plan to use the VPN connection for streaming or Kodi, there are additional steps you may need to take. This could include configuring specific settings or installing additional software or add-ons to optimize the streaming experience.
9. Money-Back Guarantee
If you are not satisfied with the FortiClient VPN and profiles deployment or if it does not meet your requirements, you may be eligible for a money-back guarantee. Be sure to check with the vendor or provider for their specific refund policy.
10. Best Practices
To ensure the best results and a successful deployment, follow these best practices:
- Remove any existing VPN connections before deploying FortiClient VPN and profiles.
- Extract the FortiClientVPN.msi file from the installation package.
- Install the necessary prerequisites, such as the Win32-AppxPackage management scripts and PowerShell.
- Run the LetsConfigMgrVPN.ps1 script to install FortiClient VPN and configure the VPN gateway.
- Run the InstallFortiClientAndProfile.ps1 script to install FortiClient VPN and create the VPN profiles.
- Reboot the devices after the installation is complete using the RebootReallySuppress.ps1 script.
- To remove the VPN connections and profiles, run the RemoveVPN.ps1 script.
Create the Transform File
Before deploying FortiClient VPN and profiles on Windows computers using Microsoft Intune, you need to create a transform file. The transform file is used to customize the installation process and configure specific settings for the FortiClient software.
To create the transform file, you can use a tool called the FortiClient Packaging Wizard. This tool allows you to create a transform file by providing a base installation package and specifying the desired settings and configurations for the FortiClient software.
Once you have the base installation package and the transform file, you can use a script to deploy FortiClient VPN and profiles via Microsoft Intune. The script will use the transform file to customize the installation process and configure the FortiClient software according to your requirements.
To create shortcuts for FortiClient VPN and profiles, you can use the “Create Shortcuts” feature in the FortiClient Packaging Wizard. This feature allows you to easily create shortcuts for FortiClient VPN and profiles on the desktop or in the Start menu, making it convenient for users to access these programs.
To configure the FortiClient VPN profile, you need to specify the FortiGate gateway address and other settings. You can do this by editing the transform file or using scripts to modify the configuration files directly.
Before deploying the FortiClient VPN and profiles, it’s a best practice to test the installation process on a test machine to ensure everything is working as expected. This will help you identify any issues or errors and make necessary adjustments before deploying on production machines.
It’s important to note that when deploying FortiClient VPN and profiles via Microsoft Intune, you need to ensure that the FortiClient software is installed on the target machines before deploying the profiles. If the FortiClient software is not already installed, you can include it in your deployment package using a script or by bundling it with the profiles.
Overall, creating the transform file and deploying FortiClient VPN and profiles via Microsoft Intune is a straightforward process that allows you to configure and customize the installation according to your specific requirements. By following the steps and best practices outlined in this guide, you can successfully deploy FortiClient VPN and profiles on Windows computers and ensure secure and reliable access to your network resources.
Creating the Installer and Uninstaller Scripts
Installer Script
The first step in deploying FortiClient VPN and profiles via Microsoft Intune is creating the installer script. This script will automate the installation process and ensure that the necessary files and configurations are in place.
To create the installer script, you can use a text editor such as Notepad or a scripting tool like PowerShell. In the script, you will need to specify the location of the FortiClient VPN MSI file, which can be found on the Fortinet support website or other trusted sources such as Amazon.
Once you have located the MSI file, you can use the command “new-itemproperty” to create a new registry key that will store the path to the MSI file.
Uninstaller Script
In addition to the installer script, you will also need to create an uninstaller script. This script will be used to remove the FortiClient VPN and profiles from the user’s device if needed.
To create the uninstaller script, you can follow a similar process as the installer script. However, instead of specifying the path to the MSI file, you will need to specify the path to the uninstaller executable.
The uninstaller executable can be found within the FortiClient installation directory, typically located within the “Program Files” or “Program Files (x86)” folders on 64-bit systems. Once you have identified the uninstaller executable, you can use PowerShell commands to create a registry key that will store the path to the uninstaller executable.
By creating both an installer script and an uninstaller script, you can easily deploy and remove FortiClient VPN and profiles via Microsoft Intune. These scripts provide a streamlined and automated process for managing FortiClient VPN installations and ensuring that the necessary configurations are in place.
Preparing Microsoft Intune
In order to deploy FortiClient VPN and profiles via Microsoft Intune, there are certain prerequisites that need to be met. Here is a step-by-step guide to prepare Microsoft Intune for the deployment process:
1. Install FortiClient VPN MSI

First, it is necessary to download and install the FortiClient VPN MSI file on the devices within your organization. This can be done by running the FortiClientVPN.msi file downloaded from the Fortinet support website. Ensure that the most appropriate version for your organization’s needs, such as 64-bit or Win32, is installed.
2. Create the Transform File
Next, create a transform file to preconfigure the FortiClient VPN profiles. This can be done by creating a new script, named “installFortiClientAndProfile.ps1” for example, and adding the necessary commands. The transform file will contain information such as the VPN gateway address and other preconfigured settings.
3. Test the Installation Process
Before deploying the FortiClient VPN and profiles to your devices, it is essential to test the installation process to ensure it works as intended. Run the script created in the previous step and check for any errors or issues that may arise. This will help identify any problems before moving forward with the deployment.
4. Remove Unwanted Programs
As part of the preparation process, it is a good practice to remove any unwanted programs or scripts that may interfere with the installation of FortiClient VPN and profiles. This can be done by running the necessary removal scripts or manually uninstalling any conflicting software.
5. Add FortiClient VPN and Profiles to Microsoft Intune
Once the prerequisites are in place and the installation process has been tested successfully, it is time to add the FortiClient VPN and profiles to Microsoft Intune. This can be done by accessing the Intune portal and navigating to the appropriate section where the VPN and profiles can be configured and deployed to the desired devices within the organization.
6. Configure VPN and Profile Settings
Within the Intune portal, configure the VPN and profile settings according to your organization’s requirements. This includes specifying the VPN gateway address, preconfigured settings, and any other necessary parameters. Take into consideration any specific requirements or restrictions, such as device type or operating system.
7. Deploy FortiClient VPN and Profiles
Lastly, deploy the FortiClient VPN and profiles to the intended devices within your organization. This can be done by selecting the devices or groups where the VPN and profiles should be installed, and initiating the deployment process. Verify that the installation is successful and that the VPN and profiles are present on the devices.
By following these steps, you can successfully prepare Microsoft Intune for the deployment of FortiClient VPN and profiles. This will ensure that your organization’s devices are equipped with secure and reliable VPN connectivity for remote access to your network.
Uploading the FortiClient VPN and Profiles to Microsoft Intune
Once you have created the transform file, you can proceed with uploading the FortiClient VPN and profiles to Microsoft Intune. This step is essential to ensure that the FortiClient VPN and profiles are available for deployment on your devices within the organization.
To upload the FortiClient VPN and profiles to Microsoft Intune, follow these steps:
- Open the Microsoft Intune portal and navigate to the “Apps” section.
- Click on “Add” to create a new app and select “Windows app (Win32)” as the app type.
- Provide a name and description for the app, such as “FortiClient VPN” and “VPN client for secure remote access.”
- In the “App package file” field, click on “Select file” and browse to the location where you have saved the FortiClient VPN transform file.
- In the “Install command” field, enter the following command: “msiexec /i forticlientvpn.msi /qn”
- In the “Uninstall command” field, enter the following command: “msiexec /x {product GUID} /qn”
- Scroll down to the “Detection rules” section and click on “Add detection rule.”
- Select “File” as the rule type and enter the file path and filename for the FortiClient VPN executable, such as “C:Program FilesFortinetFortiClientFortiClient.exe”.
- Click on “OK” to save the detection rule.
- Scroll down to the “Requirements” section and configure any additional requirements or dependencies for the app, such as a minimum operating system version or required profiles.
- Click on “Add” to create a new profile that will be associated with the FortiClient VPN app.
- Configure the desired settings for the profile, such as the VPN gateway address, authentication type, and connection timeout.
- Click on “OK” to save the profile.
- Review the summary of the app and profile settings, and click on “Create” to upload the FortiClient VPN and profiles to Microsoft Intune.
- Once the upload process is complete, you can verify that the FortiClient VPN and profiles are successfully installed by checking the installed apps and profiles list in Microsoft Intune.
By following these steps, you can easily upload the FortiClient VPN and profiles to Microsoft Intune for deployment on your organization’s devices. This enables your users to securely access the network resources they need remotely, ensuring a safe and efficient workflow.
Creating a Configuration Policy in Microsoft Intune
Creating a configuration policy in Microsoft Intune allows you to manage and deploy settings for applications and devices within your organization. This step-by-step guide will demonstrate how to create a configuration policy specifically for deploying FortiClient VPN and profiles.
Step 1: Sign in to Microsoft Intune
First, sign in to the Microsoft Intune portal using your credentials. Once logged in, navigate to the “Apps” section and select “Configuration Policies” from the side menu.
Step 2: Click “Add” to Create a New Configuration Policy
Within the Configuration Policies section, click on the “Add” button to create a new configuration policy. This will open a new window where you can define the policy settings.
Step 3: Configure General Settings
In the General Settings section, provide a name and description for the configuration policy. This will help you easily identify and understand the purpose of the policy.
Step 4: Configure App Settings
In the App Settings section, specify the necessary settings for FortiClient VPN and profiles. This may include parameters such as server address, gateway, and reporting options. Use the appropriate syntax and values depending on your specific requirements.
Step 5: Configure Additional Settings
In the Additional Settings section, you can further customize the configuration policy by adding additional parameters or values. This may include options for uninstalling previous versions, installing specific file extensions, or enabling specific features within FortiClient VPN and profiles.
Step 6: Save and Assign the Configuration Policy
After configuring all the necessary settings, click on the “Save” button to save the configuration policy. Once saved, you can assign the policy to the desired users or groups within your organization. This ensures that the FortiClient VPN and profiles are deployed to the intended recipients.
By following these steps, you can successfully create a configuration policy in Microsoft Intune for deploying FortiClient VPN and profiles. This streamlines the deployment and management process, allowing your organization to benefit from secure and efficient remote access capabilities.
Deploying the FortiClient VPN and Profiles via Microsoft Intune
When it comes to deploying the FortiClient VPN and Profiles via Microsoft Intune, there are several steps to follow.
Step 1: Create the Transform File
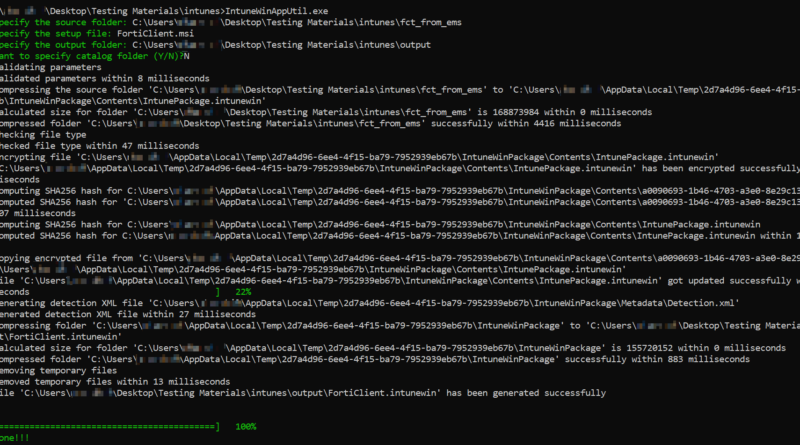
To begin, you’ll need to create a transform file that is used to customize the installation of the FortiClient VPN. This transform file will include settings such as the VPN gateway address, tunnel mode, and more.
- Use the PowerShell executable “powershellexe” to create the transform file.
- Generally, the transform file is created using the “intunewim” and “intunewim” scripts.
- Create the necessary keys and values using the “new-itemproperty” command.
Step 2: Deploy the FortiClient VPN
Once the transform file is created, you can deploy the FortiClient VPN to the target devices. This can be done using Microsoft Intune’s app store or by using a Win32 package.
- For the app store method, use the “win32” extension to upload the FortiClient VPN.
- For the Win32 package method, use the “dedicated app packager” to create the package.
- Make sure to include the transform file in the package to apply the custom settings.
Step 3: Deploy the FortiClient Profiles
After the FortiClient VPN is deployed, you can also deploy the FortiClient profiles for specific settings and configurations.
- Create a new item using the “new-itemproperty” command and specify the profile settings.
- To remove a profile, use the “remove-itemproperty” command.
- Remember to specify the correct device (e.g., iPhone, AMD64) when creating or removing profiles.
Step 4: Manage and Fine-Tune
Once the FortiClient VPN and profiles are deployed, you can manage and fine-tune the settings as needed.
- Manage the VPN gateway address, tunnel mode, and other settings through the transform file.
- Use PowerShell scripts to add or remove certain settings.
- Smart scripts can be created to streamline the management process.
- Monitor the installation and operation of the FortiClient VPN and profiles for any issues.
Step 5: Troubleshooting and Support
If any issues arise during the deployment or operation of the FortiClient VPN and profiles, troubleshooting and support resources are available.
- Refer to documentation and support materials provided by Fortinet for guidance.
- Check online forums and communities for solutions to common issues.
- Reach out to the Fortinet customer support team for direct assistance.
- Stay up to date with the latest FortiClient VPN and profiles updates to ensure the best performance and security.
Assigning the Configuration Policy to Users or Groups
Users and Groups
Once you have created the configuration policy for FortiClient VPN and profiles in Microsoft Intune, the next step is to assign it to the appropriate users or groups. Assigning the policy ensures that the necessary settings and configurations are applied to the intended users or groups.
Assigning to Users
To assign the configuration policy to specific users, you can simply select the user from the list and assign the policy. This will ensure that the FortiClient VPN and profile settings are applied to that particular user when they sign in to their device.
Assigning to Groups
If you have multiple users who require the same FortiClient VPN and profile settings, it is recommended to create groups and assign the policy to those groups. This allows you to easily manage and apply the configuration policy to a large number of users without having to assign it individually to each user.
By assigning the configuration policy to a group, all members of that group will automatically receive the FortiClient VPN and profile settings when they sign in to their devices.
Testing and Reporting
Before assigning the configuration policy to users or groups, it is advisable to test the policy on a small number of devices or users. This allows you to ensure that the settings and configurations are applied correctly and work as intended.
You can also use the reporting and management features within Microsoft Intune to track the deployment and success of the configuration policy. This provides valuable insights into which users or devices have successfully received the FortiClient VPN and profile settings.
Monitoring the Deployment in Microsoft Intune
Once you have successfully deployed FortiClient VPN and profiles via Microsoft Intune, it’s important to monitor the deployment to ensure everything is working properly. Here are some steps you can take to monitor the deployment:
1. Using IntuneWim.cmd
You can use the IntuneWim.cmd utility to monitor the deployment of the FortiClient VPN and profiles. This utility allows you to view the status of the deployment and any errors that may occur.
2. Shortcut Format
Another way to monitor the deployment is by checking the shortcut format of the FortiClient VPN. If the shortcut format is correct, it usually indicates that the deployment was successful.
3. “LetsConfigMgrVPN” Script
The “LetsConfigMgrVPN” script can be used to monitor the FortiClient VPN deployment within the ConfigMgr console. It provides detailed information about the installation process, including the status of each step.
4. RebootReallySuppress
If you are experiencing any issues with the deployment, you can try using the “RebootReallySuppress” parameter. This parameter suppresses any reboot prompts during the installation process, allowing the deployment to continue without interruption.
5. Using PowerShell.exe
You can also use PowerShell.exe to monitor the deployment. By using the “Get-Win32_InstalledPrograms” cmdlet, you can check if the FortiClient VPN and profiles are installed on the device.
6. Creating and Removing Profiles
Creating and removing profiles is another way to monitor the deployment. By creating or removing profiles, you can check if the changes are being applied correctly.
7. Throttling Script
If you want to monitor the deployment without impacting network performance, you can use a throttling script. This script allows you to control the deployment speed and ensure that it doesn’t overload the network.
8. Back to the Gratis Reporting
Once the deployment is complete, you can generate a report to see the results of the deployment. This report provides detailed information about the devices that have installed the FortiClient VPN and profiles.
By following these monitoring steps, you can ensure that the deployment of FortiClient VPN and profiles via Microsoft Intune is successful and that all devices are properly configured.
Testing the FortiClient VPN on the Managed Devices
Once the FortiClient VPN and profiles have been installed on the managed devices using Microsoft Intune, it is important to test the functionality to ensure a successful deployment. The following steps can be followed to test the FortiClient VPN:
Step 1: Open FortiClient VPN
- Locate the FortiClient VPN icon in the system tray.
- Click on the icon to open the FortiClient VPN application.
Step 2: Connect to VPN Gateway
- Within the FortiClient VPN application, click on the “Connect” button.
- Choose the appropriate VPN gateway from the available options.
- Enter the required credentials for authentication.
- Click on the “Connect” button to establish the VPN tunnel.
Step 3: Test Connectivity
- Once the VPN connection is established, test the connectivity by accessing network resources or browsing the internet.
- Ensure that the internet connection is not throttled or restricted.
- Try streaming videos or performing other bandwidth-intensive tasks to ensure smooth operation.
Step 4: Disconnect from VPN
- To disconnect from the VPN, click on the “Disconnect” button in the FortiClient VPN application.
- The VPN tunnel will be closed and the device will revert to its normal internet connection.
By following these steps, the FortiClient VPN can be tested on the managed devices to validate its functionality and ensure that it meets the desired requirements. It is recommended to perform thorough testing before deploying the VPN to all devices within an organization.
Troubleshooting the Deployment
1. Checking prerequisites
Before troubleshooting any issues with the deployment of FortiClient VPN and profiles via Microsoft Intune, it’s important to ensure that all the prerequisites are met. This includes having the latest version of FortiClient installed, making sure the necessary settings and configurations are in place, and verifying the compatibility of the device with the chosen VPN provider, such as Surfshark.
2. Verifying the installation
One common issue in the deployment process is an incomplete or faulty installation of FortiClient. To verify the installation, check if the FortiClient program files are present in the specified installation directory. Additionally, make sure the FortiClient icon is visible in the system tray.
3. Troubleshooting profile deployment
If the FortiClient profiles are not being deployed as expected, check the Intune portal to ensure that the profiles are properly created and associated with the targeted devices. Make sure the necessary settings, such as VPN server address and authentication methods, are correctly configured in the profiles.
4. Testing the VPN connection
If the FortiClient VPN connection is not established or working as intended, perform a thorough test to identify the underlying issue. This may involve checking the network settings, verifying connectivity to the VPN server, and troubleshooting any VPN-related errors or warnings that may be found in the FortiClient logs or event viewer.
5. Uninstallation and reinstallation
If all troubleshooting steps fail, consider uninstalling and reinstalling FortiClient. This can be done by using the appropriate deployment tools (such as PowerShell) and ensuring that all FortiClient files and registry entries are completely removed before reinstalling.
In conclusion, troubleshooting the deployment of FortiClient VPN and profiles via Microsoft Intune requires careful attention to the prerequisites, verifying the installation, troubleshooting profile deployment, testing the VPN connection, and considering reinstallation if necessary.
Creating an Upgrade Policy in Microsoft Intune
When deploying FortiClient VPN and Profiles via Microsoft Intune, it is important to have a proper upgrade policy in place. Here is a step-by-step guide on how to create an upgrade policy in Microsoft Intune:
Step 1: Editing the Transform File
Before creating the upgrade policy, you need to edit the transform file to ensure it includes the necessary information. This includes the profiles, Kodi, and other files that need to be installed or removed during the upgrade process.
Step 2: Creating a New Item Property
In order to create an upgrade policy, you will need to create a new item property in Microsoft Intune. This property will specify the location of the FortiClient installation files as well as the upgrade command to be used.
Step 3: Selecting the Upgrade Policy
Once you have created the item property, you can select it in the upgrade policy settings. This will ensure that the FortiClient installation files are used for the upgrade and that the specified upgrade command is executed.
Step 4: Configuring the Upgrade Policy
When configuring the upgrade policy, you can specify additional settings such as installation throttling, reboot options, and hidden installations. These settings can help ensure a smooth upgrade process without impacting the system or the user experience.
Step 5: Deploying the Upgrade Policy
After configuring the upgrade policy, you can deploy it to the desired devices or user groups. This will initiate the upgrade process and ensure that the latest version of FortiClient VPN and Profiles is installed on the target devices.
In summary, creating an upgrade policy in Microsoft Intune is a crucial step in deploying FortiClient VPN and Profiles. By following these steps and configuring the necessary settings, you can ensure a seamless upgrade process and provide the best security and management for your network.
Testing the Upgrade Policy on the Managed Devices
Once the upgrade policy has been created and deployed to the managed devices, it is important to test that the FortiClient VPN and profiles are successfully upgraded.
The first step is to check that the FortiClient MSI installer and the transform file are successfully deployed to the devices. This can be done by navigating to the Intune portal and checking the status of the deployment. Ensure that the prerequisites are met and that the installation package is available to the targeted devices.
Next, verify that the installation settings and configuration profiles are properly applied. This can be done by selecting a test device and checking the installed version of FortiClient, as well as reviewing the configuration settings within the FortiClient application.
If the FortiClient VPN and profiles are successfully installed and applied, proceed with testing the upgrade. This can be done by creating a script that initiates the upgrade process. The script should execute the FortiClient installer with the necessary parameters and wait for the installation to complete.
Once the script is created, it can be deployed to the devices and run to upgrade the FortiClient VPN and profiles. During the upgrade process, it is important to note any error messages or issues that may arise. These should be documented and reported to the appropriate teams for further investigation and resolution.
After the upgrade process is complete, verify that the FortiClient VPN and profiles have been successfully upgraded. This can be done by checking the installed version of FortiClient and reviewing the configuration settings to ensure that they have been preserved. Additionally, test the VPN connectivity to ensure that it is working as expected.
By following these steps, organizations can ensure that the upgrade policy for FortiClient VPN and profiles is successfully deployed and tested on the managed devices. This will help to ensure a smooth and seamless transition for users as they continue to access corporate resources securely via the FortiClient VPN.
Removing the FortiClient VPN and Profiles via Microsoft Intune
When it comes to removing the FortiClient VPN and profiles from devices managed by Microsoft Intune, there are several options available. Here, we will discuss the best methods to ensure the swift and efficient removal of these components.
1. Using Intune Scripts
The most straightforward method is to use Intune scripts to remove the FortiClient VPN and profiles. By creating a script and editing it with the necessary commands, you can deploy it to devices via Intune, triggering the removal process. This approach is generally quick and effective, allowing for efficient management of devices within an organization.
2. Using the Uninstall Program Function
Another option is to utilize the “Uninstall Program” function from within Intune. By selecting the FortiClient VPN and profiles from the list of installed programs, you can initiate the uninstallation process on the devices. This can be done individually or in bulk, making it a flexible and convenient method of removal.
3. Manual Removal
If none of the above options are suitable, manual removal of the FortiClient VPN and profiles is also possible. This involves navigating to the device’s settings and locating the FortiClient VPN and profiles settings. From there, you can remove them manually, ensuring a clean removal without any leftover traces.
In conclusion, removing the FortiClient VPN and profiles via Microsoft Intune can be achieved using the best methods suitable for your organization’s needs. Whether it’s using Intune scripts, the Uninstall Program function, or manual removal, you can effectively manage your devices and maintain a secure network environment.
Disabling and Deleting the Configuration and Upgrade Policies
To disable and delete the configuration and upgrade policies for the FortiClient VPN, follow the steps below:
Step 1: Show Configuration and Upgrade Policies
To view the existing configuration and upgrade policies, open the Intune portal and navigate to the desired policy section.
- For configuration policies, go to “Device configuration” > “Profiles” > “Configuration profiles”.
- For upgrade policies, go to “Device configuration” > “Profiles” > “Windows 10 Update Rings”.
Step 2: Disable and Remove Policies
Once you have located the policies, select the policies you want to disable and remove.
- To disable a configuration policy, click on the policy and choose “Disable” from the options.
- To remove a configuration policy, click on the policy and choose “Remove” from the options.
- To disable an upgrade policy, click on the policy and select “Disabled” from the Status dropdown menu.
- To remove an upgrade policy, click on the policy and choose “Unassign” from the options.
Step 3: Confirm Disabling and Deleting

Confirm the disabling and deleting actions by following the prompts and confirming your selections.
It is important to note that once a policy is disabled and removed, the associated settings and configurations will no longer apply to the devices that had the policy assigned to them.
By removing the policies, you are effectively uninstalling the FortiClient VPN application from the devices. This means that any configured VPN connections and settings will be removed from the devices.
Make sure to backup any important data or information related to the FortiClient VPN before removing the policies.
Cleaning Up the Configuration Scripts and Files
Once you have tested the installation and uninstallation scripts and files, it is best practice to clean up any unnecessary files and scripts. This ensures that only the required files are present and that the configuration is streamlined without any clutter.
Removing Unnecessary Files
To remove any unnecessary files, locate the scripts that you are no longer using for the installation or uninstallation process. Delete these files from your system to free up space and make the configuration process more efficient.
Uninstallation Script
If you have successfully completed the installation and verification process, you can remove the uninstaller script that was created during the initial setup. This script was meant to be used in case the installation needed to be rolled back, but now that the installation is stable, it can be safely removed.
Removing Hidden Files and Folders
During the installation and configuration process, temporary or hidden files and folders might have been created. It is a good practice to remove these files and folders, as they can clutter the system and potentially cause issues in the future.
Updating Documentation and Descriptions
After cleaning up the configuration scripts and files, it is important to update any documentation or descriptions related to the installation process. This will ensure that future users have accurate information and can easily follow the step-by-step guide without any confusion.
Final Testing
Once you have completed the cleanup process, it is recommended to perform a final test to ensure that the installation and uninstallation processes still work smoothly. This will give you peace of mind and confidence that the configuration is ready for deployment in a production environment.
In conclusion, cleaning up the configuration scripts and files after creating and testing the installation and uninstallation processes is an important step to ensure a streamlined and efficient deployment. By removing unnecessary files, hidden folders, and updating documentation, you can create a clean and organized configuration profile for deployment via Microsoft Intune.
Вопрос-ответ:
What is the first step to deploy FortiClient VPN and Profiles via Microsoft Intune?
The first step is to create the Transform File. This file contains the configuration settings for FortiClient VPN and Profiles.
Can I use FortiClient VPN with Microsoft Intune?
Yes, you can deploy FortiClient VPN and Profiles using Microsoft Intune. This allows you to manage and configure VPN connections on devices enrolled in Intune.
What is the purpose of the Transform File?
The Transform File contains the configuration settings for FortiClient VPN and Profiles. It specifies parameters such as server addresses, authentication methods, and connection options.
How do I create the Transform File?
To create the Transform File, you need to use the FortiClient Configurator Tool. This tool allows you to specify the desired settings and create the Transform File based on those settings.
Can I customize the VPN settings for FortiClient?
Yes, you can customize the VPN settings for FortiClient. By creating and modifying the Transform File, you can define the specific VPN settings you want to deploy via Intune.
What is the purpose of deploying FortiClient VPN and Profiles via Microsoft Intune?
The purpose is to centrally manage VPN connections on devices enrolled in Intune. By deploying FortiClient VPN and Profiles, you can ensure that devices have the necessary VPN settings for secure remote access.
How can I ensure secure remote access to my network with FortiClient VPN?
You can ensure secure remote access to your network by deploying FortiClient VPN and Profiles via Microsoft Intune. This allows you to configure and manage VPN settings on enrolled devices, ensuring a secure connection to your network.
Видео:
How to setup built in VPN client in Windows 10
How to setup built in VPN client in Windows 10 by Soft Solutions 4 years ago 3 minutes, 57 seconds 33,176 views
Intune Tutorial 24 – How to Deploy Configuration Profile – Administrative Template in Intune
Intune Tutorial 24 – How to Deploy Configuration Profile – Administrative Template in Intune by Harvansh Singh 1 year ago 18 minutes 2,463 views